Apple’s iOS Security Faustian Dilemma
The legend of Faust claims that he struck a bargain with the devil, trading his soul for limitless knowledge and pleasure. But did you know that the legend is wrong? Faust was just an iPhone owner seeking security updates for last year’s version of iOS.
***
There’s a rhythm to Apple’s software updates. Every June, Apple holds WWDC, their developer’s conference. At the event, they announce the next generation of iOS. Then, over the course of the summer, they release test versions of the new iOS, shipping the completed OS in the fall—usually mid- to late- September. Apple identifies these iterations of iOS using “semantic versioning”, a common practice in the software industry. So when you see a version number like 10.3.2:
- “10” is the “major” version number. This changes infrequently (once a year in Apple’s case) and indicates substantial changes that may not be backwards-compatible. These may be a significant user interface overhaul, removal of support for certain frameworks or types of apps, or the addition of a shiny new functionality.
- “x.3” is the “minor” version number. It changes when new functionality is added without breaking old software.
- “x.x.2” is the “patch” number. It changes when a release fixes bugs whilst adding no new features and breaking no old software.
The fall release of iOS changes the major version number—for instance, on September 19, 2017 Apple released iOS 11, replacing September 13, 2016’s iOS 10. Then, through the course of the next year, Apple releases a series of “minor” updates and “patches” to mitigate any problems that arise. But here’s the catch: Apple has never released a minor update to the previous version of iOS after the release of a new major version, nor a patch.
Apple’s non-Mac devices—the iPhone, iPad, Apple Watch, Apple TV and the upcoming Homepod—run iOS, or a variant of it. (The Watch and TV run watchOS and tvOS respectively, but under the hood they’re iOS tuned to the different hardware capabilities of their platforms.) Apple responds swiftly to urgent security problems with these OSs, releasing minor updates soon after issues become apparent. But they only do this for the most current versions. Which leaves their users with a Faustian dilemma: “Either apply a big software update that you may not want, or live with known vulnerabilities on your device.”
A Year In Security
2017 to early 2018 was a terrible year, security-wise. Four standouts:
July 2017: Broadpwn. A hardware vulnerability affecting the Wifi chipset in nearly every iPhone and Android phone was patched in 10.3.3 on July 19, 2017. Broadpwn allows an attacker to execute code on the affected device. Ars Technica estimates that Broadpwn impacted a billion smart phones.
October 2017: KRACK. A protocol vulnerability in the design of Wifi’s WPA2 protocol, which provides security for almost all modern wifi networks. KRACK allows devices to bypass Wifi authentication, joining Wifi networks they’re not authorized to be part of. This handily allows attackers inside the security perimeter established by the network’s router/firewall and lets a device mount a more thorough, more easily executed attack on individual computers on the network. Patched in iOS 11.1 on October 31, 2017.
January 2018: SPECTRE and MELTDOWN. CPU vulnerabilities that allow access to protected areas of memory. MELTDOWN was mitigated by iOS 11.2 on December 2nd (well before Meltdown was publically disclosed); SPECTRE was patched in iOS 11.2.2 on January 8. SPECTRE and MELTDOWN likely affect every iPhone ever released.
Broadpwn, SPECTRE and MELTDOWN all allow an attacker to execute code on a target computer. KRACK allows access to otherwise protected networks and resources. Best of all, if your computer is compromised by any of these vulnerabilities, you won’t know. There’s no telltale signature to look for, no tripwire to check, no bloody tracks in the snow. Compounding the severity of these issues is the fact that they are all hardware or protocol based—not bugs in the OS—which makes them omnipresent. If iOS 11 is vulnerable, so are all previous versions. But Apple’s got you covered, right?
The iOS Upgrade Dilemma
Nope - not entirely. Once Apple releases a new, major version of iOS, they never release updates for the previous major versions. From the iOS version history:
| iOS Version | Release Date | Last Update of Previous Major Version | Release Date |
| 11.0 | 19 September 2017 | 10.3.3 | 19 July 2017 |
| 10.0 | 13 September 2016 | 9.3.5 | 25 August 2016 |
| 9.0 | 16 September 2015 | 8.4.1 | 13 August 2015 |
| 8.0 | 17 September 2014 | 7.1.2 | 30 June 2014 |
When Apple fixed Broadpwn in iOS 10.3.3, iOS 9 and earlier users were still vulnerable and had to update to iOS 10 to protect themselves. When Apple fixed KRACK in iOS 11.1, iOS 10 and earlier users were still vulnerable and had to update to iOS 11 in order to protect themselves. And when Apple fixed SPECTRE and MELTDOWN in iOS 11.2 and iOS 11.2.2, iOS 10 and earlier users were still vulnerable and had to update to iOS 11 in order to protect themselves.
But while Apple enjoys rapid adoption of new iOS releases, many users lag behind or decide never to update. According to Apple, as of January 18, 2018, 65% of iOS devices were running iOS 11, 28% were running iOS 10, and 7% were running iOS 9 or earlier. That’s 35% of iOS users who are still vulnerable to KRACK, SPECTRE and MELTDOWN, and 7% who are still vulnerable to Broadpwn.
[caption id=”attachment_1490” align=”aligncenter” width=”582”]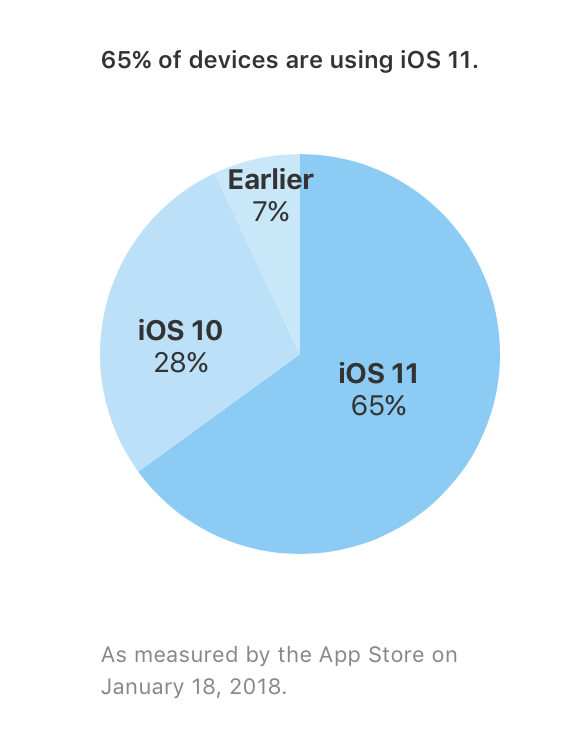 Source: Apple Developer Program App Store Support - https://developer.apple.com/support/app-store/[/caption]
Source: Apple Developer Program App Store Support - https://developer.apple.com/support/app-store/[/caption]
Which begs the question: Should we be forced to perform a major upgrade, from a version of iOS that’s a year or two old to the latest version of iOS, in order to fix major security issues?
“Why Don’t You Just Upgrade?”
Every new, major release of iOS changes some functionality, overhauls some piece of user interface and introduces some incompatibilities with some applications.
One huge change in iOS 11 is that it stopped supporting 32 bit apps. In fact, 187,000 apps were not compatible–roughly 8% of all iOS apps. While many of those apps had not been updated in a long time, or had even been abandoned, they still worked. Which meant that anyone who still used them would have to choose between continuing to use the app and staying on iOS 10, or giving up the app and moving to iOS 11. iOS 11 also changed the way app switching and killing was done, and changed the way the control panel worked. Some people like this. Others? Well, they don’t.
So, certain users may have good reasons to want to stick with iOS 10—and apparently about 22% of them still do—but at the cost of being vulnerable to attacks that they won’t be able to tell have happened. And with the recent drama about Apple reducing iOS’ demands on the CPU by slowing it on devices with degraded batteries (widely misreported as “Apple slows down old iPhones”), many iOS users simply don’t trust new releases of iOS on the older devices.
It Doesn’t Need To Be This Way
Apple does occasionally issue security updates for older versions of macOS. In fact, they released updates to both macOS 10.11 and 10.12 to mitigate SPECTRE and MELTDOWN (macOS 10.13 is the current major version when SPECTRE and MELTDOWN hit). But this is the exception, not the rule. And customers of Apple’s distinguished competition’s fare little better, and often far worse.
Google issues fewer updates to major releases of Android than Apple does, but also performs monthly security updates to Android which aren’t reflected in the Android version number. Unfortunately only Google-branded phones receive the updates immediately. Due to Android fragmentation, the the bulk of Android users are running a variety of older releases of Android with no reliable path to newer software. Many Android users never even see updates and important security fixes, or only receive them months after Google releases them. Google doesn’t issue security updates for phones three years or older.
Objectively, Google-branded Android phones receive better security updates than iOS does, while non-Google Android phones are often left wanting and much worse off than iOS devices.
User-Centric?
Apple espouses, and usually abides by, a user-centric philosophy. But in this domain, they don’t - instead, they herd users to the latest version of iOS. A three year old phone is good enough to run the latest release of iOS but one year old software is not worth having up-to-date vulnerability protection. It’s bullshit. 35% of iOS devices haven’t switched to iOS 11. As of January 2018, 1.3 billion iOS devices were in active use - that means over 455 million devices haven’t upgraded to iOS 11 yet - devices whose owners, Apple, like your products, invest in your software, propagate the success of your endeavors. These people have stuck with you. Don’t reward their loyalty with neglect. Don’t force them to make a Faustian choice between the software they want and the security they need.





